



Next: Using system or popen
Up: More Security Holes
Previous: Buffer Overruns
Contents
- Another very common problem involves the creation of files with predictable names,
typically in the /tmp directory.
- Suppose that your program prog, running as root, always creates a temporary file called /tmp/prog and writes some vital information there.
- A malicious user can create a symbolic link from /tmp/prog to any other file on the system.
- When your program goes to create the file, the open system call will succeed.
- However, the data that you write will not go to /tmp/prog; instead, it will be written to some arbitrary file of the attacker's choosing.
- This kind of attack is said to exploit a race condition. There is implicitly a race between you and the attacker. Whoever manages to create the file first wins.
- One attempt at avoiding this attack is to use a randomized name for the file. For example, you could read from /dev/random to get some bits to use in the name of the file.
- This certainly makes it harder for a malicious user to guess the filename, but it doesn't make it impossible. The attacker might just create a large number of symbolic links, using many potential names. Even if she has to try 10,000 times before wining the race condition.
- Another approach is to use the O_EXCL flag when calling open. This flag causes open to fail if the file already exists.
- Unfortunately, if you're using the Network File System (NFS), or if anyone who's using your program might ever be using NFS, that's not a sufficiently robust approach because O_EXCL is not reliable when NFS is in use.
- One approach that works is to call lstat on the newly created file.
- The lstat function is like stat, except that if the file referred to is a symbolic link, lstat tells you about the link, not the file to which it refers.
- If lstat tells you that your new file is an ordinary file, not a symbolic link, and that it is owned by you, then you should be okay.
- This attack doesn't create any direct harm, but it does make it impossible for our program to get its work done. Such an attack is called a denial-of-service (DoS) attack.
- The http://siber.cankaya.edu.tr/SystemsProgramming/cfiles/temp-file.c program in Fig. 11.5 presents a function that tries to securely open a file in /tmp.
Figure 11.5:
Create a Temporary File.
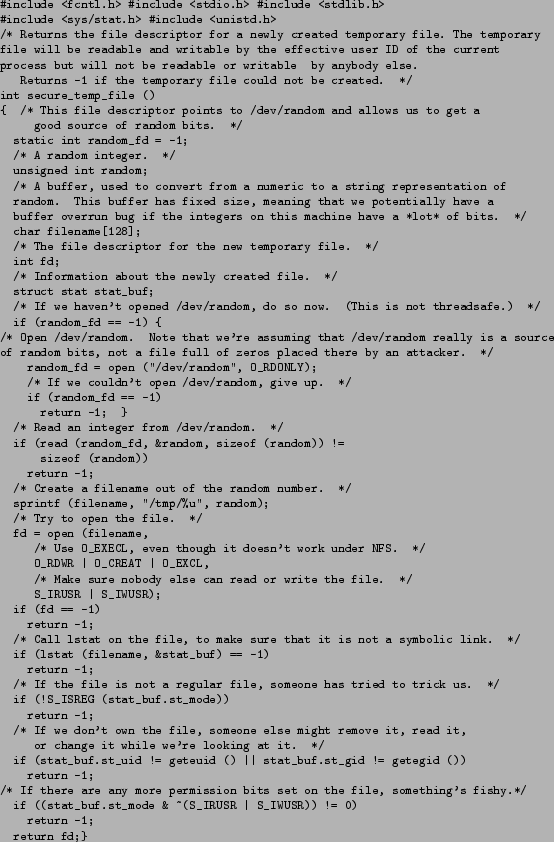 |
- This function calls open to create the file and then calls lstat a few lines later to make sure that the file is not a symbolic link.




Next: Using system or popen
Up: More Security Holes
Previous: Buffer Overruns
Contents
Cem Ozdogan
2007-05-16
