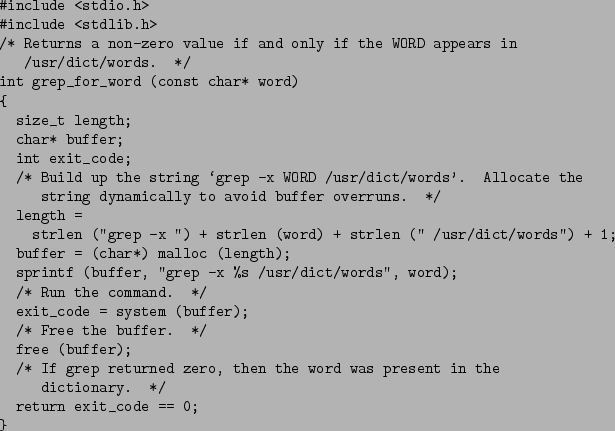
$ grep -x word /usr/dict/words
- But what happens if a malicious hacker sends a "word" that is actually the following line or a similar string?
foo /dev/null; rm -rf / grep -x foo /dev/null; rm -rf / /usr/dict/words
- One is to use the exec family of functions instead of system or popen. That solution avoids the problem because characters that the shell treats specially (such as the semicolon in the previous command) are not treated specially when they appear in the argument list to an exec call.
- The other alternative is to validate the string. In the dictionary server example, you would make sure that the word provided contains only alphabetic characters, using the isalpha function. If it doesn't contain any other characters, there's no way to trick the shell into executing a second command.